Full-Crypto setup with GRUB2
Update on 2014-03-03: quoting Colin Watson from the comments:
Note that this is spelled GRUB_ENABLE_CRYPTODISK=y in GRUB 2.02 betas (matching the 2.00 documentation though not the implementation; not sure why Andrey chose to go with the docs).
Since several people asked me how to get such a setup and it’s poorly documented (as in: I found it in the GRUB sources) I decided to blog about this. When using GRUB >=2.00-22 (as of February 2014 available in Debian/jessie and Debian/unstable) it’s possible to boot from a full-crypto setup (this doesn’t mean it’s recommended, but it worked fine in my test setups so far). This means not even an unencrypted /boot partition is needed.
Before executing the grub-install commands execute those steps (inside the system/chroot of course, adjust GRUB_PRELOAD_MODULES for your setup as needed, I’ve used it in a setup with SW-RAID/LVM):
# echo GRUB_CRYPTODISK_ENABLE=y >> /etc/default/grub # echo 'GRUB_PRELOAD_MODULES="lvm cryptodisk mdraid1x"' >> /etc/default/grub
This will result in the following dialog before getting to GRUB’s bootsplash:
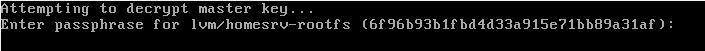
February 28th, 2014 at 13:08
Sehr cool, ty! (:
February 28th, 2014 at 13:18
This isn’t quite a full-crypto setup: Grub itself is not encrypted and could be replaced by a Trojan.
February 28th, 2014 at 13:33
For Neal:
You can use SecureBoot to ensure GRUB integrity
February 28th, 2014 at 18:22
I’ve been using that in large scale (as in a few thousand clients) since it hit the GRUB repo, I think it was about two years ago and it works quite fine. I also don’t need to use PRELOAD_MODULES.
February 28th, 2014 at 18:30
Does GRUB have support for passing the passphrase to Linux, to avoid entering it twice?
February 28th, 2014 at 20:14
@Neal: as Al noted, SecureBoot/TPM might be what you’re searching for (and your BIOS, CPU,… might also include a Trojan *cough*)
@Lukas: interesting, thanks for your real-life feedback, appreciated! :)
@Anonymous: nope, not that I’d be aware of
March 3rd, 2014 at 12:53
Note that this is spelled GRUB_ENABLE_CRYPTODISK=y in GRUB 2.02 betas (matching the 2.00 documentation though not the implementation; not sure why Andrey chose to go with the docs).
March 3rd, 2014 at 15:55
@Colin: oh, thanks for the heads up, highly appreciated!
regards,
-mika-
March 6th, 2014 at 19:32
I’m confused; you’re saying an unencrypted /boot is not necessary, but how does grub get its configuration and modules, then? Bit of a hen and egg problem there, in my head.
March 7th, 2014 at 23:44
@towo: AFAICT only the code to actually get access to your crypted /boot (or rootfs if you don’t have a separate /boot partition) is in the MBR, no further config (or unneeded modules)